Portal
Portal sign-in and authorization for web services can be performed by any OAuth2 provider that supports the required flow, such as Azure AD or Auth0.
To do this, the respective OAuth2 provider must be configured in the server. The configured provider provides the authorization for the portal and the use of the web services in the context of the portal. To configure the provider, use the Admin Portal. Select Portal and then OAuth from the toolbar.
In contrast to the authorization of web services ("Client Crendentials Flow"), in the case of the portal, the application itself establishes the authorization via the OAuth2 provider. For this purpose, the portal uses the OAuth2 flow "Authorization Code Flow With Proof Key for Code Exchange (PKCE)" to obtain the corresponding authorization.
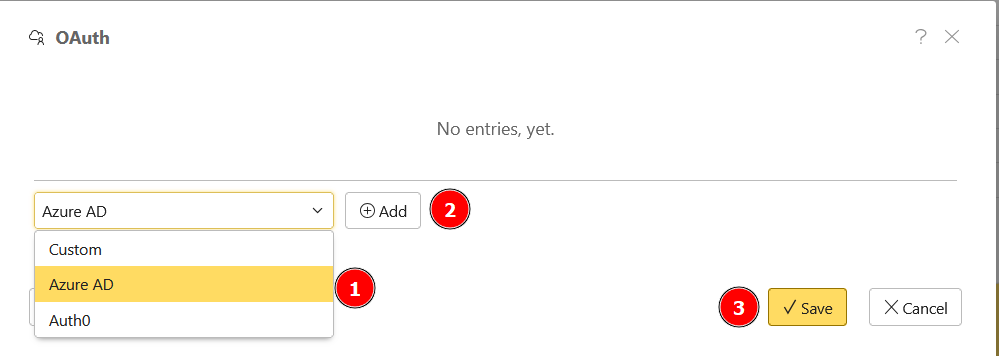
In the dialog, select the corresponding provider from the list (1) and add it with Add (2).
In the following dialog, you have to enter the values of the selected provider. To do this, you must first make the appropriate settings on the OAuth2 provider's side and enter the configured values in the dialog.
The portal is a "Single Page Application" (SPA). The settings must therefore be made accordingly on the OAuth provider side.
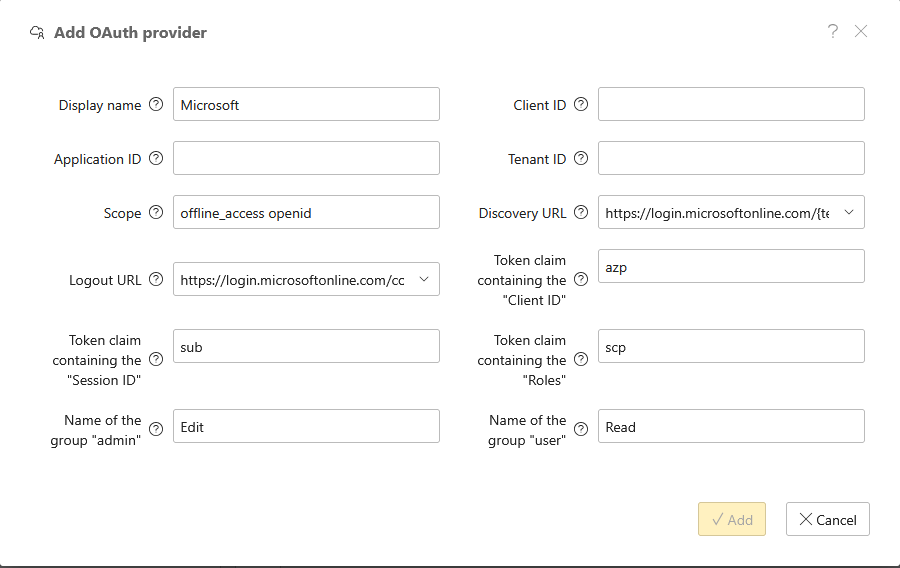
Depending on the OAuth provider selected, certain fields may already be filled in with default values (see the Azure AD example above). As a rule, you must at least fill in the Client ID, Application ID and Tenant ID and, if necessary, add a Scope. You define these on the OAuth provider's page or can determine them there.
If you select Custom as the OAuth provider, you must enter all details manually.
For example, the creation of an App registration for Azure Ad.
After all values have been entered, you can save them by clicking on Save. The settings will be applied after the server is restarted.
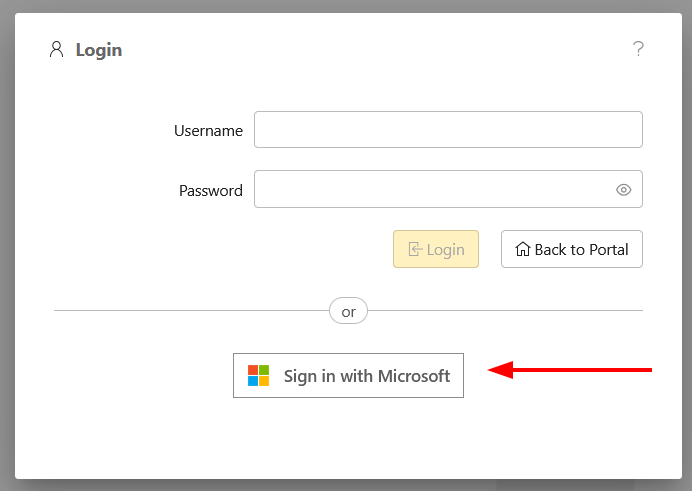
Login dialog
If an OAuth2 provider is configured for the portal, it appears as an additional login option in the portal login dialog.
Login dialog with Azure AD as OAuth2 provider for portal login: