Portal Auth0
To log in to the Portal using single sign-on and Auth0, you have to set up an application and API in the Auth0 admin center.
Create API
The first step is to create an API under Applications. Create a new API with Create API, enter the Name (1) and define a unique Identifier (2).
The Identifier for Auth0 corresponds to the Application ID for the later configuration in the server.
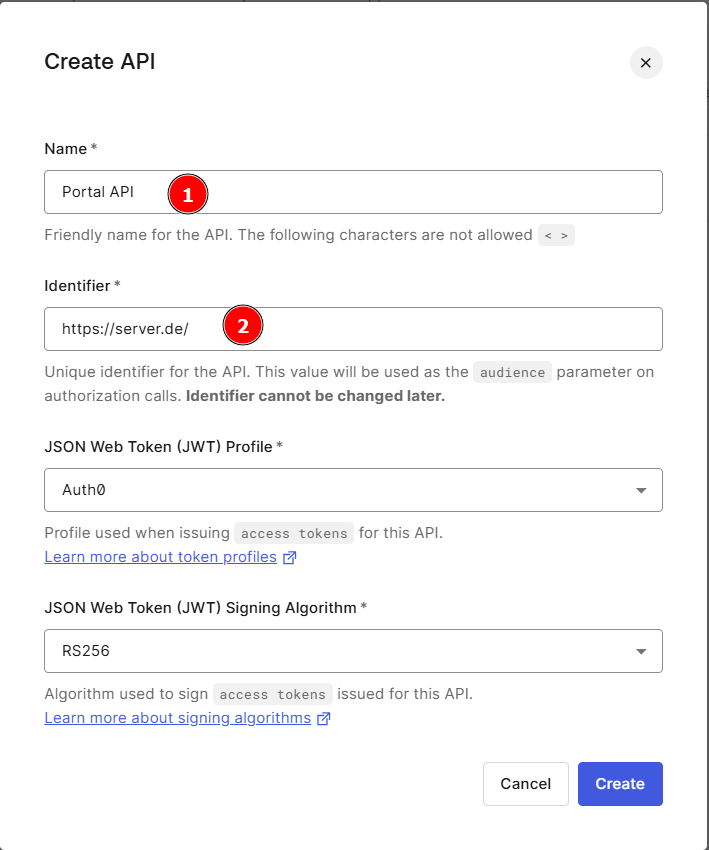
The other settings can be adopted unchanged so that the API is created.
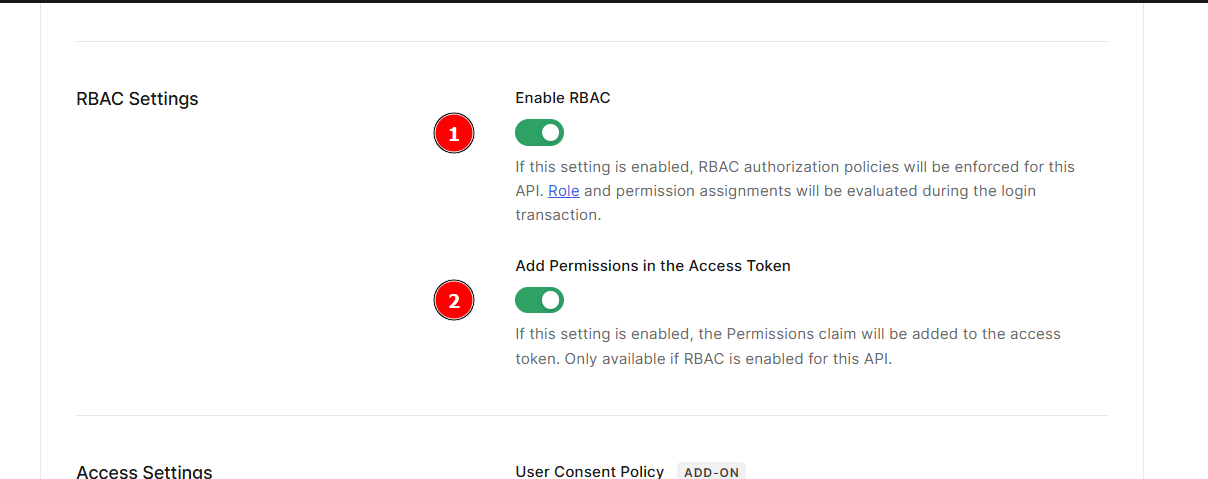
On page Settings please activate the options Enable RBAC and Add Permission in the Access Token under RBAC settings.
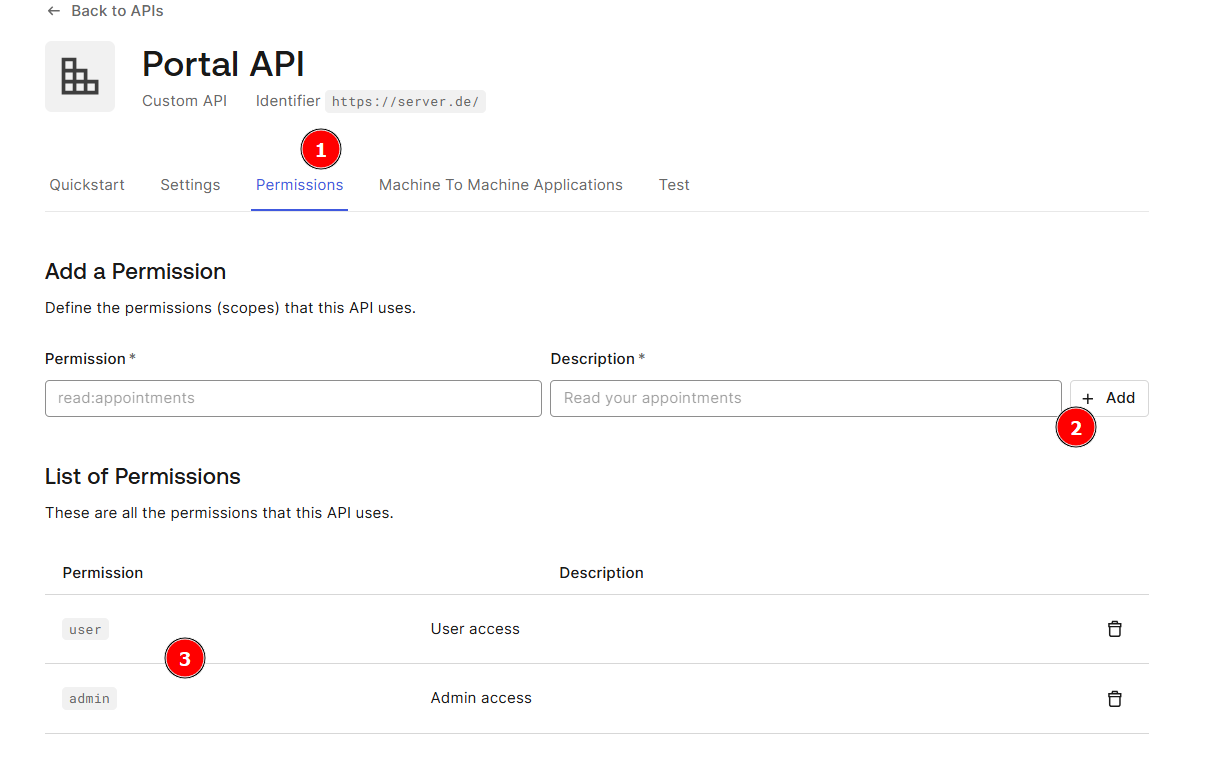
Create the two permissions user and admin (3) under Permissions (1) with Add (2).
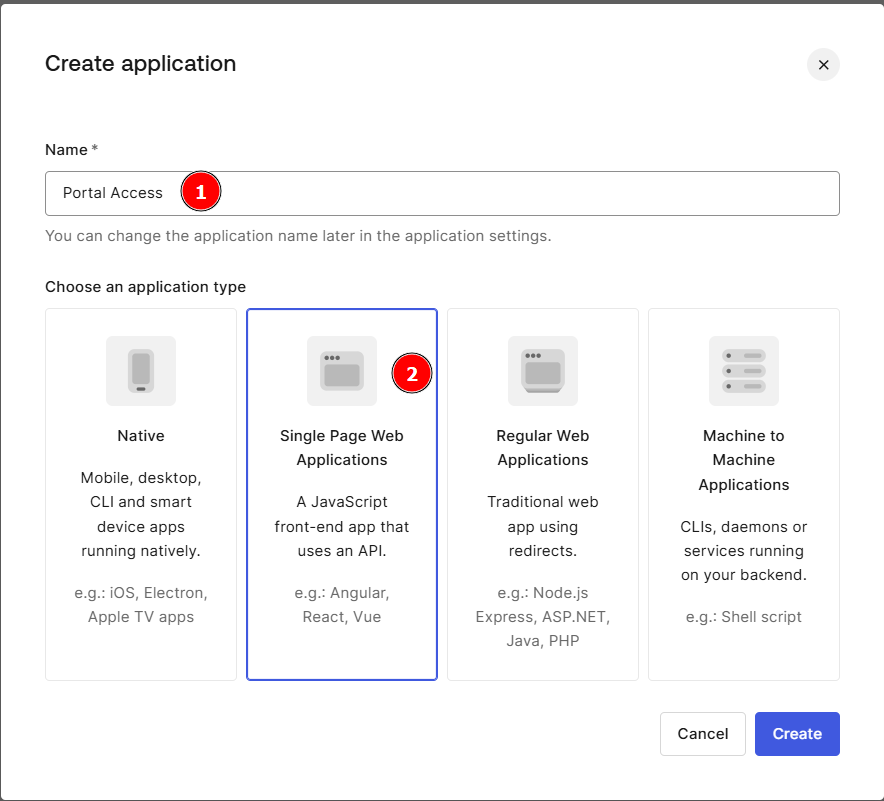
Create Application
Create a new application under Applications with Create Apllication. Specify a Name (1) and select Singe Page Web Application (2) as the type.
After the application has been created, you will see the Basic information on the Settings page (1).
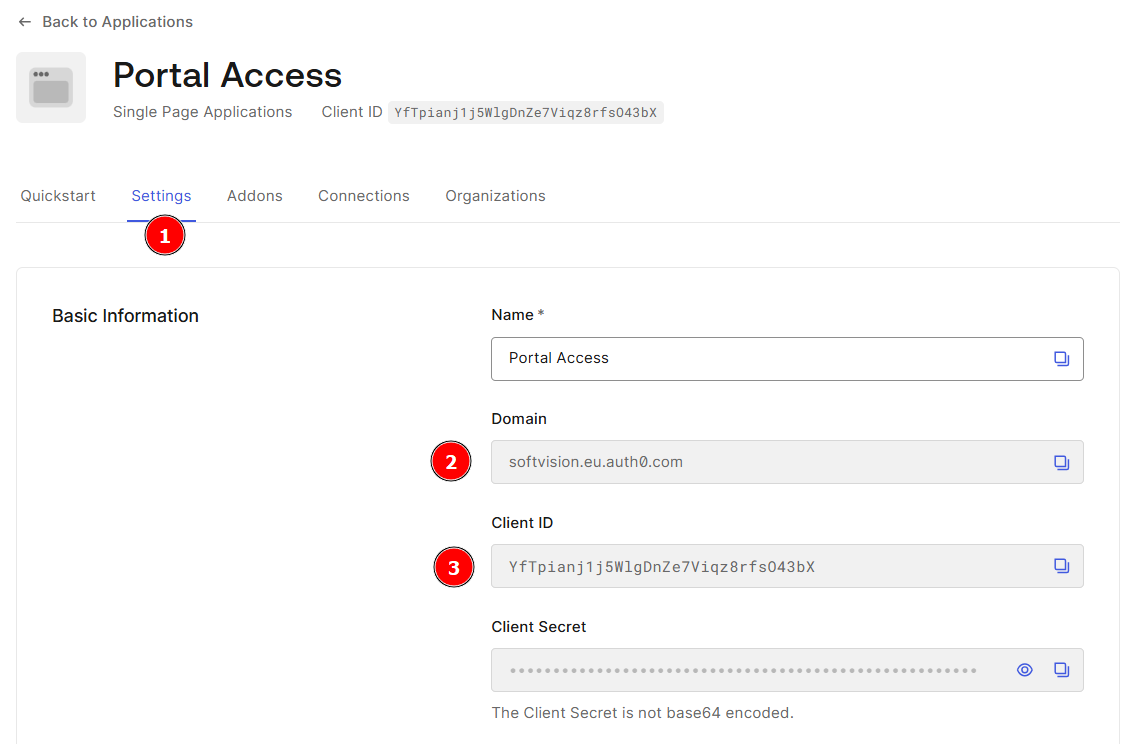
Make a note of the Domain (2) (is the Tenant ID) and the Client ID (3) for later configuration in the server.
Then go down to the Settings page and enter the Allowed Callback URLs under Applications URI's (1):
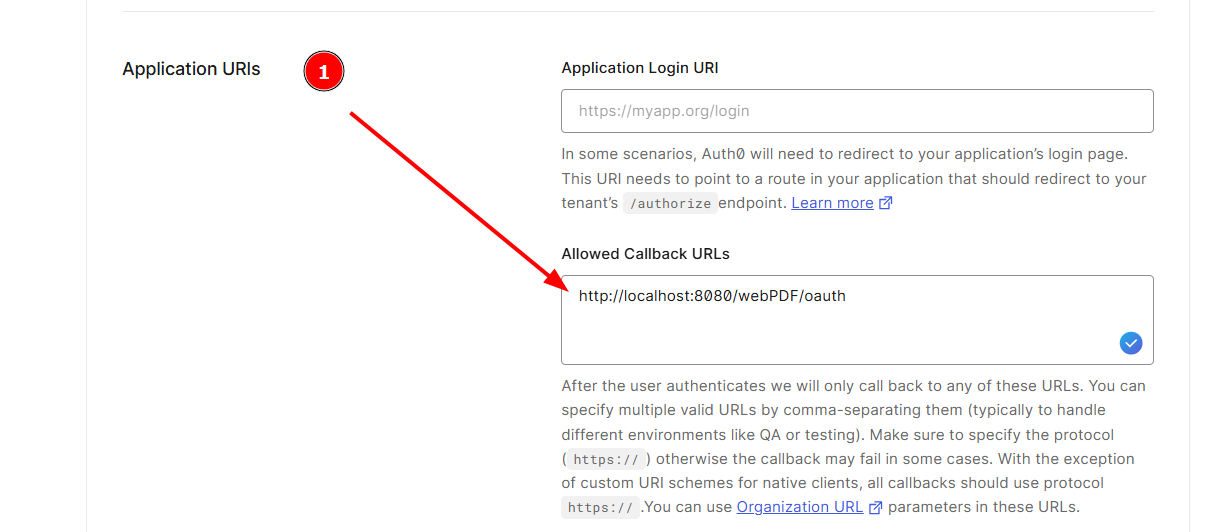
The definition of the URI is necessary because the portal is a Single Page Application (SPA) which, after logging in on the provider side, requires the executed login to be able to call up the web services. After successfully logging in to the OAuth provider, the user is redirected to this page to log in to the portal.
The URI must be defined for your server and end with /webPDF/oauth.
Example: http://localhost:8080/webPDF/oauth
Save the changes.
If you also want to support the logout from the OAuth provider in the portal, you must enter the URL of the webPDF server (e.g. http://localhost:8080/webPDF/) in the application under Settings in Application URIs in Allowed Logout URLs.
Assign API to user
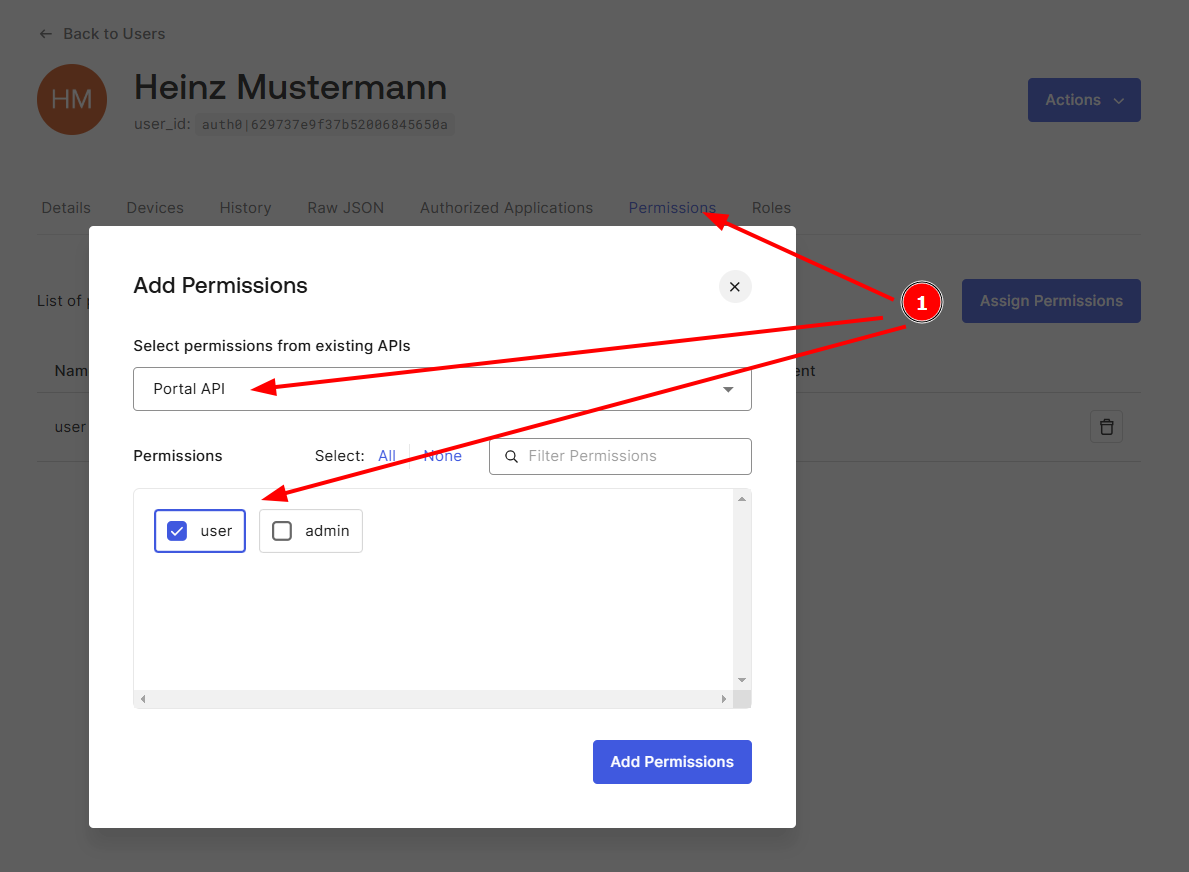
Don't forget that you must assign the defined API to the user and grant the corresponding permissions.
To do this, go to the user and add the API with Assign Permissions (1). Also select the desired authorizations for the user.
Server configuration
Once the application and API have been created, the defined values can be set in the server's Admin portal.
The provider Auth0 can be selected and created via the Portal toolbar under OAuth. The corresponding values for the application must be entered in the dialog.
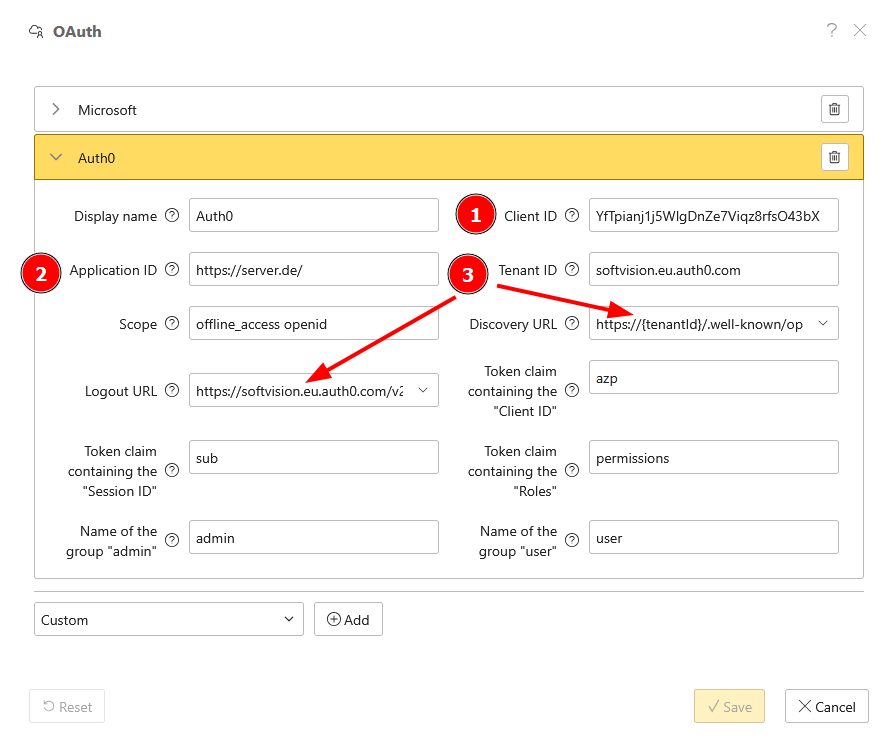
Enter the Client ID (1), the Application ID (2) and the Tenant ID (3) from the application.
The Teanant ID is the Domain under which your Auth0 account was created and is used when the application is created.
Enter the Discovery URL, which is displayed in the Auth0 application under Settings -> Advanced Settings and there under Endpoints at OpenID Configuration.
Optionally, you can also adjust the logout URL to the Domain of the application if you want to enable an Auth0 logout via the portal.
The remaining values are the default values of the Auth0 OAuth provider.
The names of the permissions in the application API can be changed under Name of group '...' if you do not want to use the default names.
After all values have been adjusted, the values must be accepted with Add and the server restarted. The additional login is then available in the login dialog.
Auth0 in the configuration file
Below is an example of the configuration in conf/server.xml for the Auth0 OAuth provider. The variables {....} must be replaced with the values from the configured App registration.
<oauth>
<providers>
<provider name="auth0"
displayName="Auth0"
flow="authorizationCodeWithPkce"
id="auth0_authorize"
tenantId="{YOUR_TENANT_ID}"
clientId="{YOUR_CLIENT_ID_OF_REGISTERED_APPLICATION}"
applicationId="{YOUR_ID_OF_REGISTERED_APPLICATION}"
scope="offline_access openid"
discoveryUrl="https://{YOUR_TENANT_ID}.auth0.com/.well-known/openid-configuration"
claimSessionId="sub"
claimClientId="azp"
claimRoles="permissions"
roleNameAdmin="admin"
roleNameUser="user">
<!-- https://auth0.com/docs/authenticate/login/logout/redirect-users-after-logout -->
<logout url="https://softvision.eu.auth0.com/v2/logout?returnTo={redirectUrl}&client_id={clientId}"/>
</provider>
</providers>
</oauth>